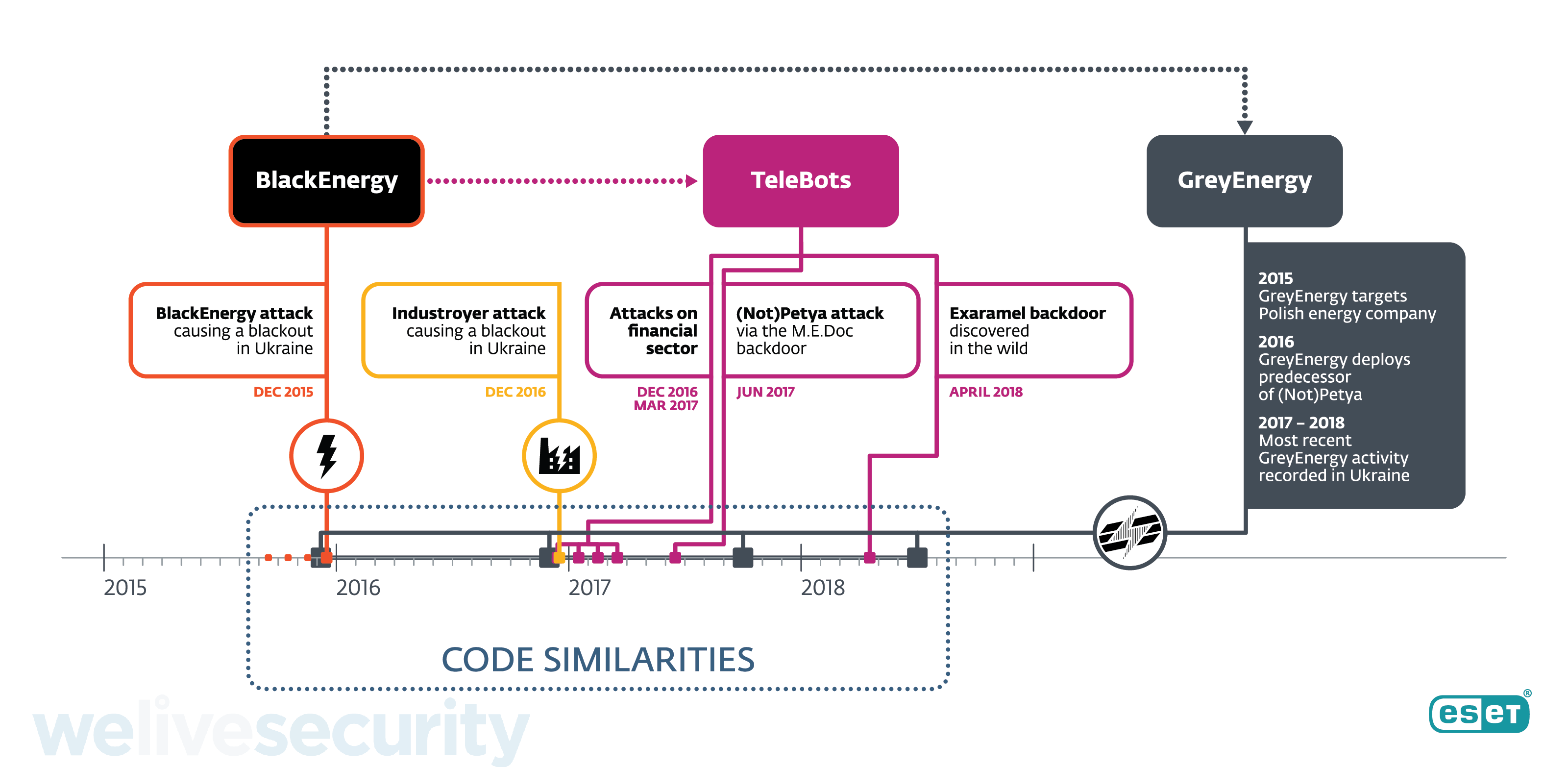
Recent ESET research has uncovered details of the successor of the BlackEnergy APT group, whose main toolset was last seen in December 2015 during the first-ever blackout caused by a cyberattack. Around the time of that breakthrough incident, when around 230,000 people were left without electricity, we started detecting another malware framework and named it GreyEnergy. It has since been used to attack energy companies and other high-value targets in Ukraine and Poland for the past three years.
GreyEnergy’s malware framework bears many similarities to BlackEnergy, as outlined below. It is similarly modular in construction, so its functionality is dependent on the particular combination of modules its operator uploads to each of the targeted victim systems. The modules that we have observed were used for espionage and reconnaissance purposes (i.e. backdoor, file extraction, taking screenshots, keylogging, password and credential stealing, etc.).
The appearance of GreyEnergy in the wild coincides with the disappearance of BlackEnergy.
We have observed two distinct infection vectors: “traditional” spearphishing, and the compromise of public-facing web servers.








