Following a six-month-long investigation, Bellingcat and its investigative partners The Insider and Der Spiegel were able to discover a hitherto secretive group of dozens of military engineers with an educational and professional background in missile programming. Phone metadata shows contacts between these individuals and their superiors spiked shortly before many of the high-precision Russian cruise missile strikes that have killed hundreds and deprived millions in Ukraine of access to electricity and heating.
The group, which works from two locations – one at the Ministry of Defence headquarters in Moscow and another at the Admiralty headquarters in St. Petersburg – is buried deep within the Russian Armed Forces’ vast “Main Computation Centre of the General Staff”, often abbreviated as ГВЦ (GVC).
Most members identified by Bellingcat and partners are young men and women, including one husband-and-wife couple, many with IT and even computer-gaming backgrounds. Some also worked at Russia’s military command centre in Damascus in the period between 2016 and 2021, a timeframe during which Russia deployed cruise missiles in Syria. Others are recipients of various military awards, including from Russian President, Vladimir Putin.
The identification of this clandestine group within the Ministry of Defence was made by parsing through open-source data of thousands of graduates of Russia’s leading military institutes that focus on missile engineering and programming, in particular the Balashikha-based Military Academy of Strategic Missile Forces near Moscow, and the Military-Naval Engineering Institute based in the Pushkin suburb of St. Petersburg.
Bellingcat analysed leaked employment or telephone entry data on these graduates available via Russia’s underground data markets.
Notably, all of these military missile engineering graduates with a GVC reference linked to their phone numbers in these apps were registered as living and working at Znamenka Street 19 in Moscow — the official address of Russia’s Armed Forces General Staff.
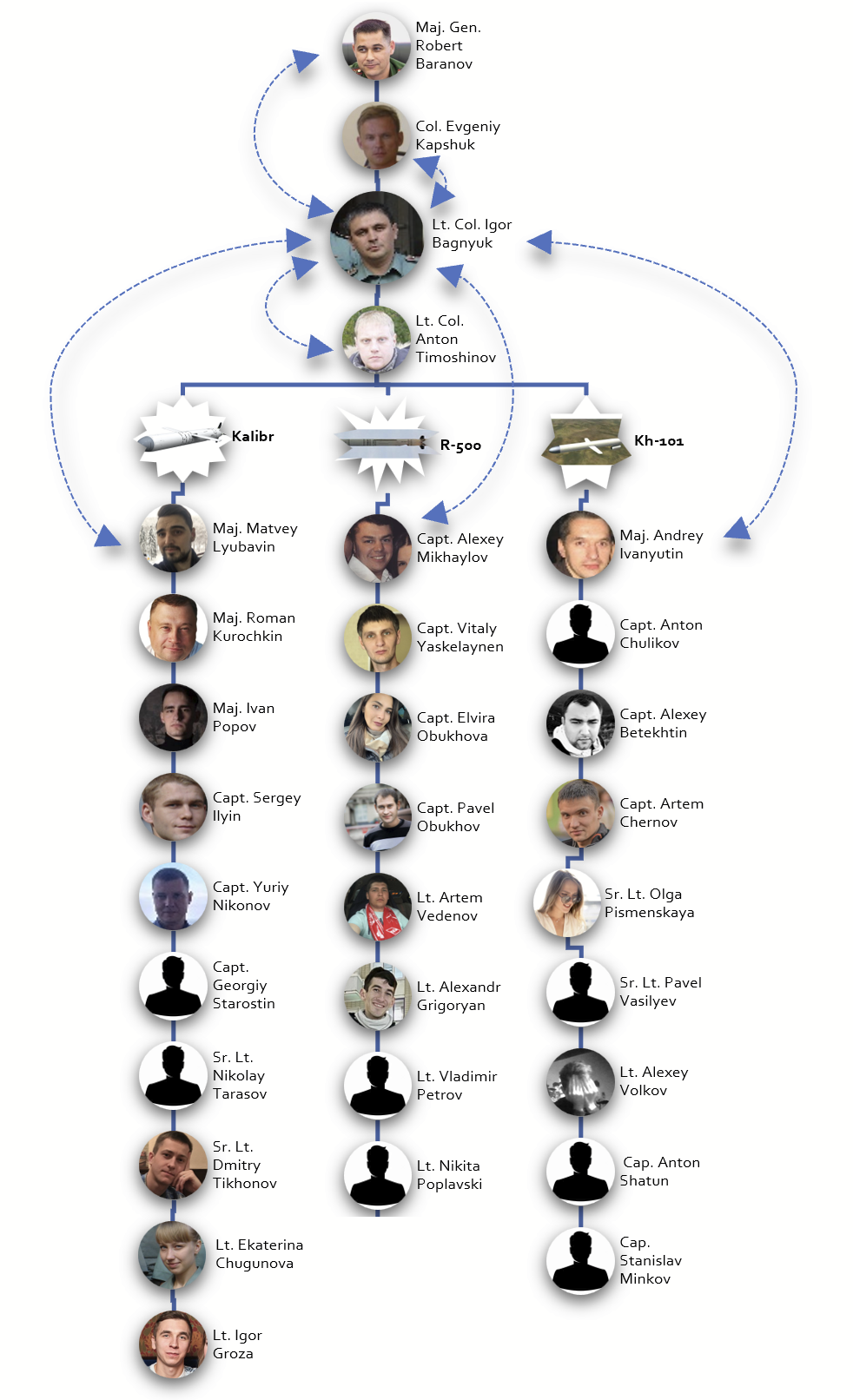
An analysis of 126 phone calls from 24 February to the end of April 2022 showed a correlation between significant Russian cruise missile attacks in Ukraine, and incoming calls prior to the missile strikes coming from one particular number that we identified as belonging to another senior officer working at the GVC. This officer is identified via phone contact listings and leaked residential databases as Lt. Col. Igor Bagnyuk, and was registered at the same address as the other known GVC officers at Znamenka 19.
By analysing the cumulative body of phone records, Bellingcat reconstructed a team of 33 military engineers who appeared to report or communicate frequently with Lt. Col. Bagnyuk.